Beware of the phishing and email scams. The greater part 58 percent of respondents expressed their associations had seen an expansion in phishing assaults in the previous year. In spite of that expansion, most organizations didn’t feel arranged to ensure themselves against phishing tricks. Without a doubt, a slight dominant part 52 percent expressed they were “not sure” in their officials’ capacity to effectively detect a phishing trick.
The development of phishing assaults in both recurrence and refinement, as verified by Verizon in its 2016 Data Breach Investigations Report, represents a noteworthy risk to all associations. It’s critical that all organizations know how to recognize probably the most well-known phishing tricks in the event that they are to secure their corporate data.

What is phishing and email scams?
Email Phishing and email scams tricks are done online by educated extortionists and wholesale fraud hoodlums. They utilize spam, counterfeit sites built to seem to be indistinguishable to genuine locales, email and texts to deceive you into revealing delicate data, similar to financial balance passwords and charge card numbers. When you take the phisher’s snare, they can utilize the data to make counterfeit records in your name, destroy your credit, and take your cash or even your character.
How to beware of phishing and email scams?
This style of data fraud is to a great degree across the board due to the simplicity with which clueless individuals share individual data. Phishing tricks frequently draw you with spam email and texts asking for you to “check your record” or “affirm your charging address” through what is really a malevolent Web webpage. Be exceptionally wary. Phishers can just discover you on the off chance that you react.
Why to beware of phishing and email scams?
After you’ve reacted to a phishing trick, the assailant can:
- Capture your usernames and passwords
- Take your cash and open Mastercard and financial balances in your name
- Demand new record Personal Identification Numbers (PINs) or extra Mastercards
- Make buys
- Include themselves or an assumed name that they control as an approved client so it’s less demanding to utilize your credit
- Get loans
- Utilize and manhandle your Social Security number
- Pitch your data to different gatherings who will utilize it for unlawful or illicit purposes
How to save yourself from phishing and email scams?
Phishers regularly put on a show to be honest to goodness organizations. Their messages may sound honest to goodness and their destinations can look astoundingly like the genuine article. It can be difficult to differentiate, however you might manage a phishing trick on the off chance that you see the accompanying.
- Solicitations for secret data by means of email or text
- Passionate dialect utilizing alarm strategies or dire solicitations to react
- Incorrectly spelled URLs, spelling botches or the utilization of sub-spaces
- Connections inside the body of a message
Absence of an individual welcome or modified data inside a message. Genuine messages from banks and charge card organizations will regularly incorporate fractional record numbers, client name or secret key.

Things to keep in mind to get rid of phishing and scams email
When your arm yourself with data and assets, you’re more astute about PC security dangers and less helpless against phishing trick strategies. Find a way to sustain your PC security and improve phishing insurance immediately. Try not to give individual data to any spontaneous solicitations for data
Just give individual data on destinations that have “https” in the web address or have a bolt symbol at base of the program. On the off chance that you think you’ve gotten phishing trap, contact the organization that is the subject of the email by telephone to watch that the message is true blue. Sort in a trusted URL for an organization’s site into the address bar of your program to sidestep the connection in a suspected phishing message. Keep in mind all the above mentioned things and beware of phishing and email scams.
Utilize shifted and complex passwords for every one of your records. Persistently check the exactness of individual records and manage any errors immediately. Stay away from sketchy Web destinations. Practice safe email convention. Try not to open messages from obscure senders. Promptly erase messages you think to be spam. Ensure that you have the best security programming items introduced on your PC for better phishing assurance. Utilize antivirus assurance and a firewall
Get antispyware programming assurance
An unprotected PC resembles an open entryway for email phishing tricks. For a more intense type of security, utilize a spam channel or portal to filter inbound messages. Items like Webroot Spy Sweeper® and Webroot Internet Security Essentials frustrate risky malware before it can enter your PC, stand protect at each conceivable passageway of your PC and battle off any spyware or infections that attempt to enter, even the most harming and mischievous strains. While free hostile to spyware and antivirus downloads are accessible, they can’t stay aware of the ceaseless surge of new spyware strains. Beforehand undetected types of spyware can regularly do the most harm, so it’s basic to have up-to-the-minute, ensured assurance.
Particular sorts of phishing
Phishing tricks fluctuate broadly as far as their multifaceted nature, the nature of the phony, and the aggressor’s goal. A few particular kinds of phishing have developed.
Lance phishing
Phishing assaults coordinated at particular people, parts, or associations are alluded to as “stick phishing”. Since these assaults are so pointed, aggressors may try really hard to assemble particular individual or institutional data in the expectation of making the assault more authentic and improving the probability of its prosperity.
The best protection against skewer phishing is to deliberately, safely dispose of data that could be utilized as a part of such an assault. Further, know about information that might be generally effortlessly realistic (e.g., your title at work, your most loved spots, or where you bank), and think before following up on apparently arbitrary solicitations by means of email or telephone.
Whaling
The expression “whaling” is utilized to depict phishing assaults (generally stick phishing) coordinated particularly at official officers or other prominent focuses inside a business, government, or other association.
Maintain a strategic distance from tricks
To make preparations for phishing tricks, think about the accompanying:
Indiana University and other respectable associations will never utilize email to ask for that you answer with your secret key, full Social Security number, or private individual data. Be suspicious of any email message that requests that you enter or confirm individual data, through a site or by answering to the message itself. Never answer to or tap the connections in such a message. On the off chance that you figure the message might be true blue, go specifically to the organization’s site or contact the organization to check whether you truly do need to make the move depicted in the email message.
The most secure practice
Phishing messages frequently contain interactive pictures that look honest to goodness; by perusing messages in plain content, you can see the URLs that any pictures point to. Moreover, when you enable your mail customer to peruse HTML or other non-content. Just designing, assailants can exploit your mail customer’s capacity to execute code. It leaves your PC powerless against infections, worms, and Trojans. In the event that you read your email in HTML organize.
Drift your mouse over the connections in each email message to show the real URL. Check whether the drift content connection coordinates what’s in the content, and whether the connection resembles a site with which you would typically work together. Beware of phishing and email scams.
On an iOS gadget, tap and hold your finger over a connection to show the URL. Lamentably, Android does not as of now bolster this.
Before you click a connection, verify whether the message sender utilized a computerized signature when sending the message. A computerized signature guarantees that the message really originated from the sender.
When you perceive a phishing message, first report it as noted underneath. After that erase the email message from your Inbox, and afterward purge it from the erased things envelope. It will maintain a strategic distance from coincidentally getting to the sites it focuses to. Beware of phishing and email scams.
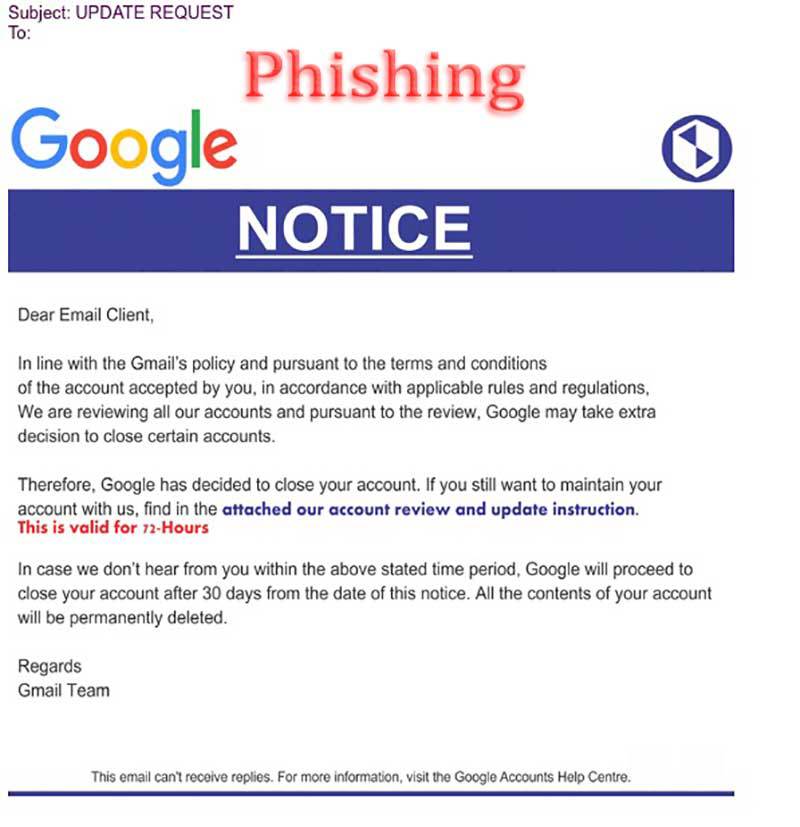
Warnings
Beware of phishing and email scams today. Perusing email as plain content is a general best practice. That while staying away from some phishing endeavors, won’t evade them all. Some authentic destinations utilize divert contents that don’t check the sidetracks. Therefore, phishing culprits can utilize these contents to divert from honest to goodness destinations to their phony locales.
Another strategy is to utilize a homograph assault. It because of International Domain Name (IDN) bolster in present day programs. It enables aggressors to utilize distinctive dialect character sets to deliver URLs that look astoundingly. See Don’t Trust Your Eyes or URLs.
